Privacy by Design
Everyone that has kids—or ever was a kid—knows that the best way to avoid trouble is not to put yourself in a position where trouble is likely to find you in the first place.  In the privacy realm, this means taking steps at the outset to minimize risk of exposure and mitigate the potential consequences of a breach or other inadvertent disclosure. The recently discovered database breach at Epsilon demonstrates how vulnerable personally identifiable information can be to unauthorized access and theft. For a third party vendor such as Epsilon, the consequences of these types of exposures are particularly wide reaching—potentially extending across an entire client base—exposing multiple brands not just to security concerns but to customer discontent. In the last couple of days, companies including Target, Kroger, TiVo, US Bank, Home Shopping Network, Ameriprise Financial, LL Bean, Visa Card, Brookstone, Walgreens, Disney Destinations, and Best Buy have notified their own customers about the breach.
In the privacy realm, this means taking steps at the outset to minimize risk of exposure and mitigate the potential consequences of a breach or other inadvertent disclosure. The recently discovered database breach at Epsilon demonstrates how vulnerable personally identifiable information can be to unauthorized access and theft. For a third party vendor such as Epsilon, the consequences of these types of exposures are particularly wide reaching—potentially extending across an entire client base—exposing multiple brands not just to security concerns but to customer discontent. In the last couple of days, companies including Target, Kroger, TiVo, US Bank, Home Shopping Network, Ameriprise Financial, LL Bean, Visa Card, Brookstone, Walgreens, Disney Destinations, and Best Buy have notified their own customers about the breach.
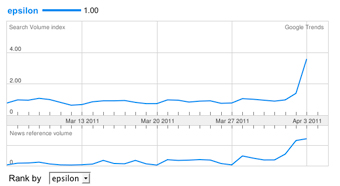
Google trends shows a dramatic spike in searches for “Epsilon” in the last few days.
In its 2010 report on the protection of consumer privacy, the FTC emphasized the importance of “Privacy by Design”—an approach that proposes that privacy assurance cannot solely be based on compliance with regulatory frameworks but should ideally stem from organization’s default mode of operation. The FTC identified a number of substantive protections that it said were of “critical importance to consumer privacy.” Specifically, they called upon companies to put in place physical, technical and administrative safeguards to protect consumer information and to limit data collection to what is necessary for legitimate business needs. Only that data which is strictly necessary to accomplish the product goals should be collected and it should be retained for only such a period as it is relevant.
Companies that collect and store any consumer data should regularly review the sensitivity of the data, the size and nature of a company’s business, and the types of risk the company faces and develop appropriate safeguards based on those factors. Most importantly, these discussions need to occur at the product design phase and not as an afterthought in response to a breach.
![Screen shot 2011-04-05 at 11.26.01 AM[1]](https://richrelevance.com//wp-content/uploads/2011/04/Screen-shot-2011-04-05-at-11.26.01-AM1-640x275.png)
User discontent has flooded social media airwaves with anti-Epsilon epithets.

